by Marco Lettieri | News
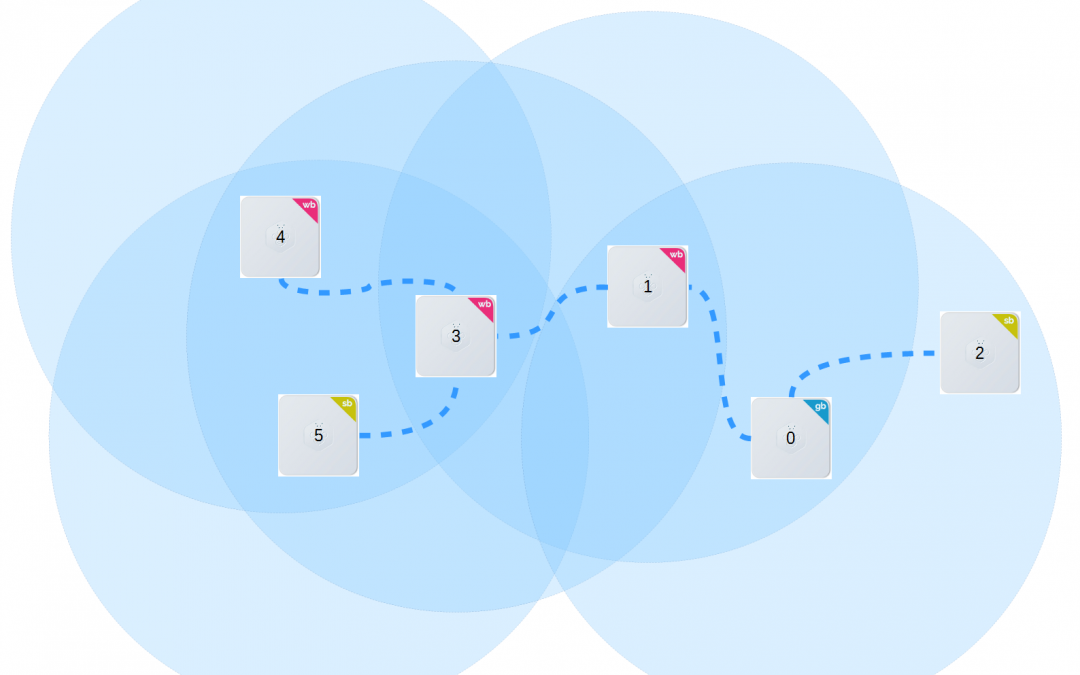
How a BEEs network works BEEs talk to each other via our sub-GigaHz radio protocol called 'BeeTalk'. BEETalk protocol (patent pending) is: secure - we use a cryptographic Hash algorithms to protect the radio packet against "Man on the middle" smart - discovers the network and choose the best path with mesh support - every node of the network can [...]

by Marco Lettieri | News
Android's permission system is one of the biggest security concern all along since those permissions are asked for at install time. Once installed, the application will be able to access all of things granted without any user's acknowledgement what exactly application does with the permission. In Marshmallow, apps -- at least those that have been [...]




